Enhance Security Services
Expert security services for small and medium organizations to minimize risk and enhance security posture.
Application Security
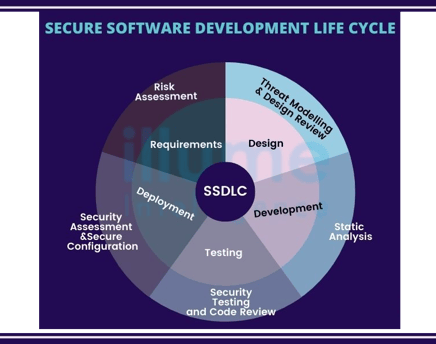
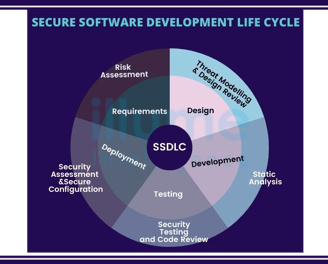
Safeguarding Your Software Ecosystem
Regarding application security, SecureMode will work with your team to understand your current practices and provide a tailored approach/recommendation that seamlessly integrates security.
We aim to implement a secure-by-design process that includes secure coding practices, regular security assessments, and integrating security into the software development lifecycle.
SecureMode's arsenal is versatile. We use a comprehensive combination of security tools, including SAST, DAST, IAST, SCA, and RASP, to identify and address a wide range of security vulnerabilities.
Application Security
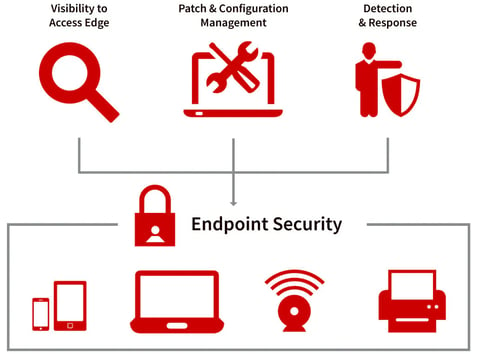
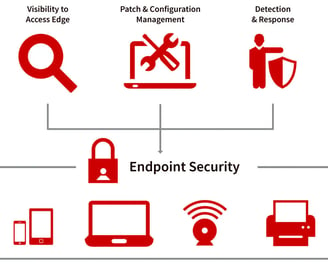
Endpoint Security
Shielding Your Last Line of Defense
Change always brings new opportunities and challenges. The rise of the remote workforce and advancements in technology have led to the use of various endpoint devices.
Endpoint devices, including laptops, tablets, mobile phones, and other wireless devices, are not just tools for productivity. When connected to corporate networks, they can also serve as potential attack paths for security threats, underscoring the need for robust security measures.
That is where SecureMode comes into play. We work with your team to understand the scope and network and design / implement security solutions that align with the business goals.
Application Security
Endpoint Security
Strengthening Your Security Posture
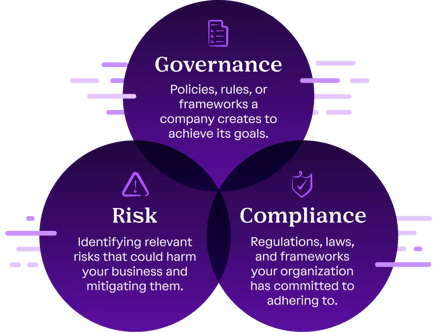
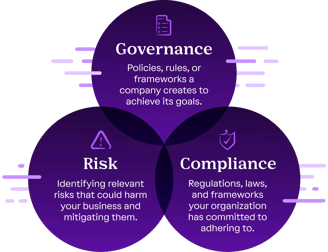
In today's fast-evolving digital landscape, effective Governance, Risk, and Compliance (GRC) services are essential for organizations aiming to navigate complex regulatory environments while minimizing risks and achieving strategic objectives.
SecureMode GRC services encompass a comprehensive approach to managing the intertwined aspects of GRC, we starts by assessing your existing policies and processes, along side industry best practices and cutting-edge technology, identifying gaps and vulnerabilities that may expose your organization to unnecessary risks.
Moreover, our GRC services extend beyond mere compliance and risk management; they are designed to add strategic value to your organization
Governance Risk & Compliance
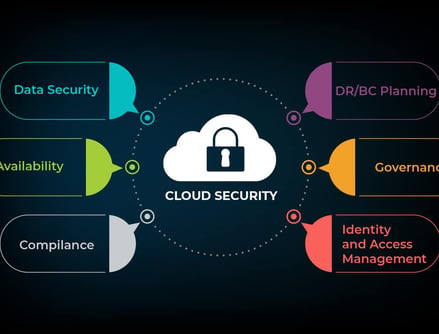
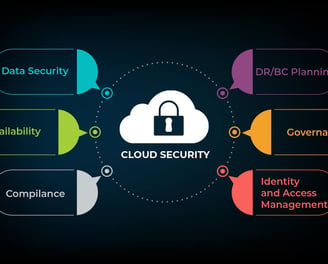
Cloud Security
Empowering Your Business with Confidence
In an era where digital transformation is paramount, secure cloud services offer businesses the agility, scalability, and efficiency needed to thrive in a competitive market. However, as organizations migrate to the cloud, ensuring the security of sensitive data and critical operations becomes a top priority
SecureMode approach to secure cloud services is rooted in a deep understanding of the unique challenges and risks associated with cloud environments. We encourage the implementation of multi-layered security measures to ensure complete coverage and scope of the environment.
Beyond security, our service ensures your company fully complies with industry regulations and best practices.
Cloud Security


Data Security
Safeguarding Your Most Valuable Asset
In today's digital age, data is the lifeblood of any organization, driving decisions, innovation, and growth. However, with the increasing sophistication of cyber threats, protecting this invaluable asset has never been more critical.
SecureMode comprehensive approach to data security begins with a thorough assessment of your current security posture, identifying vulnerabilities and potential risks within your infrastructure.
Beyond safeguarding your data, our consulting services focus on empowering your organization with the knowledge and tools needed to manage data security proactively. We provide ongoing support, training, and updates to ensure that your team is equipped to handle emerging threats and regulatory requirements
Protecting the Future of Intelligent Systems
As artificial intelligence (AI) becomes increasingly integral to business operations, securing these intelligent systems is crucial to maintaining trust and safeguarding against evolving cyber threats. AI systems, with their ability to process vast amounts of data and make autonomous decisions, are powerful tools that drive innovation and efficiency. However, their complexity and connectivity also make them vulnerable to sophisticated attacks.
SecureModeI will forward approach to AI security begins with a deep understanding of the unique risks associated with AI technologies. From adversarial attacks that can manipulate AI algorithms to data poisoning that compromises the integrity of AI training data, we address the full spectrum of threats that could impact your AI systems.
Beyond protecting your AI systems from threats, our consulting services focus on ensuring the ethical and responsible use of AI within your organization.
Artificial Intelligence Security
Email Security
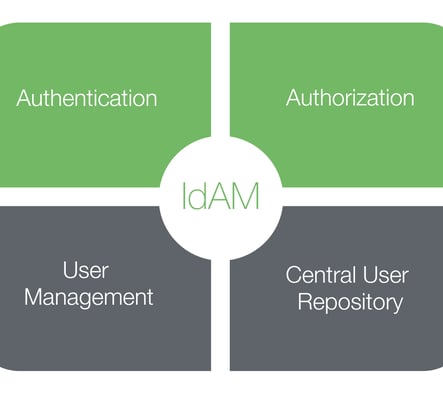
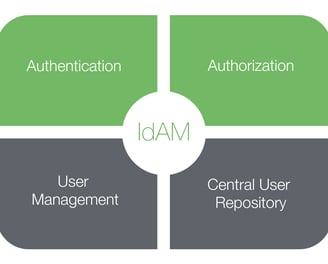
Identity & Access Management [IDAM]
Control, Protect, and Empower
In an increasingly digital world, managing who has access to your critical systems and data is more important than ever. Identity and Access Management (IAM) is at the heart of modern cybersecurity, providing the foundation for secure access control and protecting your organization from unauthorized access.
Our IAM services cover the entire spectrum of identity and access management, from initial assessment and strategy development to implementation and ongoing management. We work closely with your team to understand your unique needs and challenges, crafting a customized IAM strategy that aligns with your business goals.
Beyond technical implementation, our IAM services emphasize the importance of compliance and governance. We help you establish clear policies and procedures for managing identities and access rights, ensuring that your organization meets all relevant regulatory requirements.
Email Security


Defending Your Communication Channels
Email remains one of the most vital communication tools for businesses, but it is also a primary target for cybercriminals. Phishing attacks, malware distribution, and data breaches are just a few of the threats that can compromise your email system, leading to severe financial and reputational damage. Our email security services are designed to protect your organization from these ever-evolving threats, ensuring that your communication channels remain secure and trustworthy.
Our approach to email security combines advanced threat detection with proactive defenses to keep your organization safe. We suggest state-of-the-art security technologies, robust data loss prevention (DLP) tools and process improvement
Beyond technical solutions, our email security services extend to user education and training, recognizing that employees are often the first line of defense against email-based threats.
Fortifying Your Digital Backbone
In today’s interconnected world, the security of your network and IT infrastructure is the cornerstone of your organization’s overall cybersecurity strategy. With the increasing complexity of network environments and the growing threat landscape, ensuring the integrity, availability, and security of your infrastructure is more critical than ever.
Our approach to network and infrastructure security begins with a thorough assessment of your existing environment, identifying vulnerabilities and potential risks. We then design and implement a robust security framework that includes advanced firewalls, intrusion detection and prevention systems, and secure network architecture. Our services extend to continuous monitoring and real-time threat detection, ensuring that any suspicious activity is quickly identified and mitigated.
In addition to protecting your network, our infrastructure management security services focus on optimizing your IT environment for efficiency and scalability.
Network & Infrastructure Security
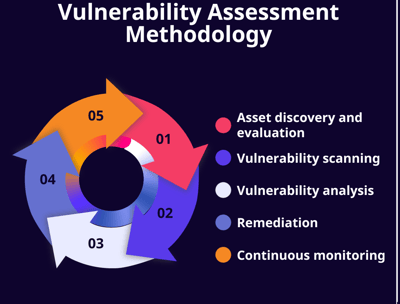
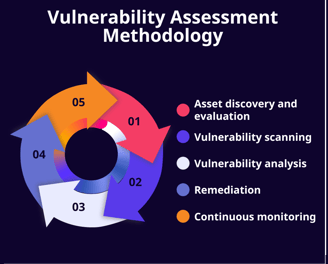
Vulnerability Management
Managing Your Risk Exposure
In an era of sophisticated cyber threats, proactively identifying and addressing vulnerabilities is essential to safeguarding your organization’s assets and data. Vulnerability management is at the heart of a resilient cybersecurity posture, ensuring that potential weaknesses are detected, prioritized, and remediated before they can be exploited.
Our comprehensive vulnerability management services start with an in-depth assessment of your digital ecosystem, uncovering security gaps across applications, systems, and networks. Leveraging industry-leading tools and threat intelligence, we conduct continuous vulnerability scans and risk assessments, prioritizing findings based on potential impact and exploitability. Beyond detection, we provide actionable insights and work closely with your team to implement effective remediation strategies, from timely patching to configuration adjustments.
With a proactive vulnerability management approach, your organization can stay ahead of emerging threats, improve compliance, and fortify its defenses, building a secure foundation for business continuity and growth.
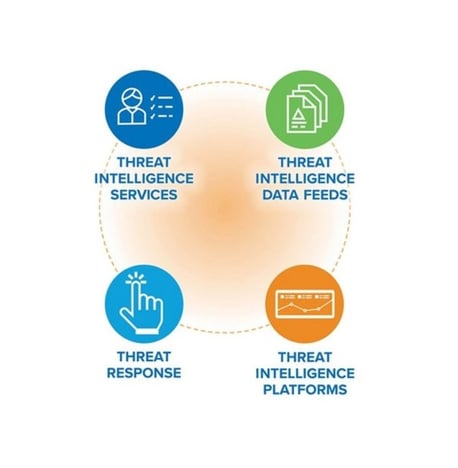
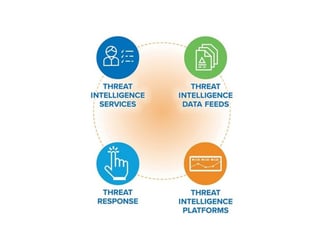
Rapid Response to Secure Your Operations
In today’s fast-moving digital landscape, the ability to respond quickly and effectively to security incidents is critical to minimizing damage and protecting sensitive data. Our Incident Response services provide a structured, rapid-response approach to detect, contain, and remediate security incidents.
Starting with a thorough analysis of the event, we identify the root cause and scope of the incident to mitigate its impact. Our team then implements containment strategies and recovery steps to ensure your operations return to normal swiftly and securely. Post-incident, we deliver detailed reports and actionable insights to strengthen your defenses and prevent future incidents. With a resilient Incident Response strategy in place, your organization can maintain business continuity and mitigate the long-term impact of security breaches.
Advanced Threat Analysis to Stay Ahead of Adversaries
In a constantly evolving threat landscape, understanding and anticipating potential threats is key to maintaining a strong security posture. Our Threat Analysis services deliver deep insights into the tactics, techniques, and procedures (TTPs) used by cyber adversaries, allowing your organization to anticipate and neutralize threats before they escalate.
Using advanced threat intelligence and behavioral analysis tools, we continuously monitor for signs of malicious activity, providing real-time alerts and actionable intelligence tailored to your environment. Our team conducts in-depth analysis to assess the potential impact and severity of threats, helping prioritize responses and guide strategic security decisions. With robust Threat Analysis, your organization can stay one step ahead, improving threat visibility, enhancing situational awareness, and building a proactive defense against emerging cyber risks.
Incident Response & Threat Intelligence
Security Awareness and Training
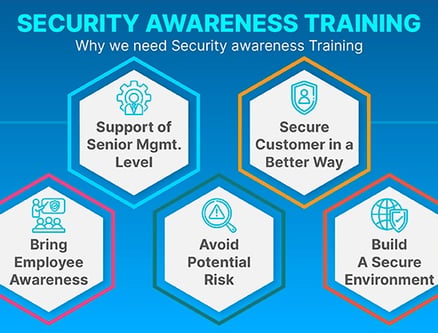
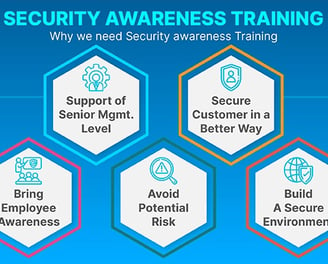
Empowering Your Workforce with Security Awareness Training
In today’s threat landscape, your employees are the first line of defense against cyber threats. Our Security Awareness Training program equips your workforce with the knowledge and skills to recognize and respond to potential security risks, fostering a culture of vigilance and responsibility.
Our training curriculum is designed to be engaging and relevant, covering essential topics like phishing, password security, social engineering, and secure data handling practices. Through interactive modules, real-world scenarios, and regular assessments, we ensure that employees understand the impact of their actions on organizational security and stay updated on the latest threat trends.
By empowering your team to identify and prevent security incidents, Security Awareness Training enhances your organization’s resilience, reduces risk, and promotes a proactive security mindset across all levels
API Security
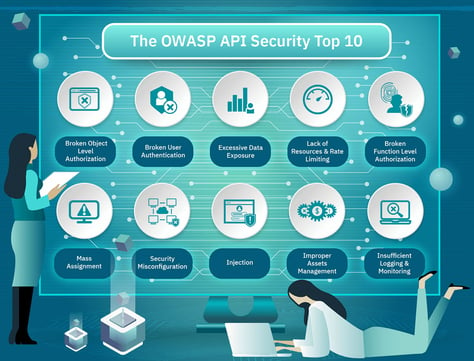
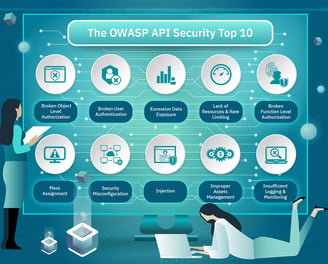
Securing Your Data Flow with Robust API Security
APIs are the backbone of modern applications, enabling seamless data exchange and integration across systems. However, this connectivity also introduces potential security risks that must be proactively managed. Our API Security services are designed to protect your APIs from unauthorized access, data breaches, and other threats, ensuring the integrity and confidentiality of your data.
We start by assessing your API landscape to identify vulnerabilities and implement security best practices such as authentication, authorization, rate limiting, and encryption. Our approach includes real-time monitoring and automated threat detection to identify unusual activity and block potential attacks before they can cause harm.
With a comprehensive API Security strategy, your organization can safely extend its digital ecosystem, empowering innovation while safeguarding critical data and maintaining trust with users.
IoT Security
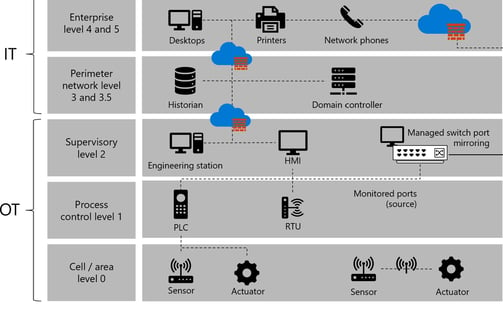
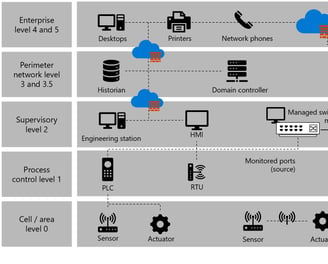
Securing IoT Through Collaboration
As IoT adoption grows, so do security risks, making it essential to protect interconnected devices from cyber threats. Effective security starts with strong authentication, encryption, and continuous monitoring to prevent unauthorized access and data breaches. Ensuring that devices are regularly updated and patched also helps mitigate vulnerabilities.
Collaboration between IT teams, device manufacturers, and security professionals is key to building a resilient IoT ecosystem. Implementing secure device provisioning, network segmentation, and real-time threat detection strengthens defenses against attacks. By integrating security from the start, organizations reduce risks and enhance overall protection.
Ongoing monitoring and adaptive security measures help keep IoT environments secure as threats evolve. Leveraging industry best practices, advanced analytics, and automated security responses ensures that businesses stay ahead of potential cyber risks while maintaining the efficiency and scalability of their IoT solutions.
Physical Security


Securing Your Data Physical Environment
Understanding the vulnerabilities in your physical security is the first step to ensuring a safe and secure environment. Our physical security assessment services are designed to uncover potential risks and gaps in your current defenses. We conduct thorough evaluations of your facilities, including access controls, surveillance systems, perimeter security, and emergency response plans. Leveraging industry standards and best practices, we provide detailed insights and actionable recommendations to strengthen your physical security posture and protect your assets, employees, and visitors.
Customized Strategies for Enhanced Protection
Every facility is unique, and our assessments are tailored to address your specific operational needs and challenges. Our experts collaborate closely with your team to identify critical assets and prioritize areas of concern. From risk identification to mitigation planning, we offer a roadmap to enhance your physical security effectively and efficiently. With our trusted expertise, you can gain peace of mind knowing that your organization is prepared to detect, deter, and respond to physical security threats with confidence.
